Two IT specialist topics in statistics as "greatest threats to the development" of companies
Mehr Statistiken finden Sie bei Statista
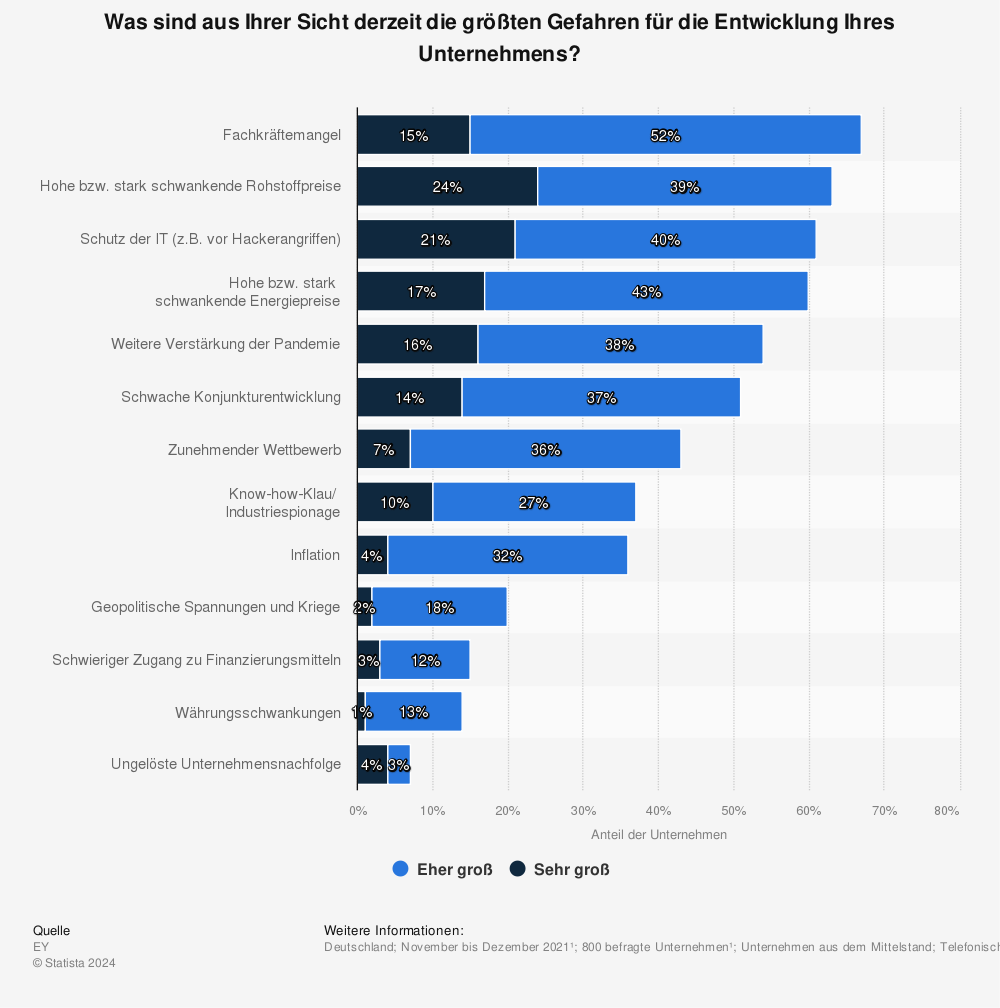
Medium-sized companies are obviously afraid of "hacker attacks" (40%) and "know-how theft" as well as "industrial espionage" (22%) when it comes to IT issues. This is the result of a survey by Statista in January 2020.
Justified concerns?
In principle, special attention should always be paid to IT security. After all, you don't leave your front door open and only expect good things. Industrial espionage is often automated these days.
Also known in the IT security area as "Signal Intelligence" (SIGINT), secret services are also working on automatic screening, storage and utilization of information that is sometimes critical to the company, as we learned from the Snowden documents published in 2013 and the NSA investigation committee of the 18th Bundestag. So-called "contractors" organized under private law work for the US foreign intelligence agency NSA. These include Companies that specialize in the detection and exploitation of vulnerabilities.
What to do?
This question should best be asked and answered before any kind of compromise. A start is, for example, following best practice approaches. A large number of attack methods can be warded off by a uniformly high level of security, which is not only based on best practices. For example, password managers can ensure that passwords that are difficult to guess can be used for online services. Because one of the biggest mistakes when using Internet services or generally computer-related authorization procedures is the use of the same (and weak) password. With the help of a password manager, a new secure password, consisting of many characters, numbers and special characters for a service, can be created in a user-friendly and simple manner and called up and be reused using a master password.
For example, password managers can ensure that passwords that are difficult to guess can be used for online services.
But is that enough to protect yourself from online threats?
Usually the answer is no.
How your own IT infrastructure is made up, e.g. the structure of your networks, how they are separated safely, but also how and whether you give users and devices access to resources, and how to secure and archive them are major variables in this equation.
Therefore the motto is: Never consider IT security as a luxury good, but plan and implement holistic systems from the outset.
IT security and the general planning of networks and resources is a red flag for many medium-sized companies. Often there is simply a lack of specialists who can cover these areas of responsibility. That is why we at LOGIT Systems. Solutions. have been taking on these tasks for our medium-sized customers since 2014, such as at Nappo & Moritz GmbH in NRW and nationwide.
As an innovative company with expertise in ever new technologies, we also enable our customers to turn new challenges into opportunities.
